In our previous NMAP tutorial, we have seen how to identify web application firewall using NMAP. Today we will learn how to evade web application firewall and IPS using NMAP. NMAP provides lot of options that help in bypassing or evading firewalls when scanning for targets. We will see multiple different ways of evading web application firewall and IPS using NMAP.
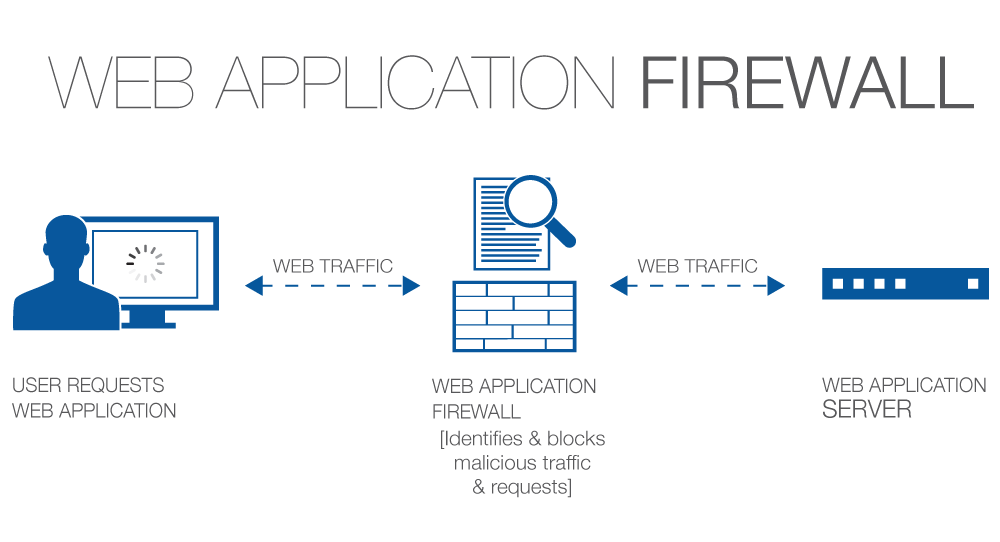
Ways to Evade Web Application Firewall and IPS using NMAP:
Note : We will using our KALI Linux (attacker machine) and Vulnerable_VM (OWASP-bwa server – target machine) in this tutorial. Start both virtual machines that we setup for our Penetration testing. For more details refer to tutorial : Setting up own penetration testing Lab.
Evading WAF/IPS Using ACK Scan :
Nmap support multiple scan types like Connect Scan(by default), ACK Scan,TCP scan, UDP scan etc.. ACK Scan is used to bypass rules on some routers that only allow SYN packets from internal networks, thus blocking default connect scan. These routers will only allow internal clients to make connection through the router and will block all packets originating from the external network with a SYN bit set. When the ACK scan option is invoked with the –sA flag, Nmap generates the packet with only ACK bit set; fooling the router into believing that the packet was a response to a connection made by an internal client and allows the packet through it. The ACK scan option cannot tell state of the port i.e. whether a port at the target system is open or closed. But it can very well tell that response is filtered or unfiltered; hence it can be used to identify online systems behind the router.
We can run ACK scan in NMAP as follows. Open Kali Linux and issue the below command in terminal to run ACK scan :
nmap -sA 192.168.56.102

We can very well see that our Vulnerable_VM server is not filtering any port.
Hardcoded originating ports in Firwall Rules :
Hardcoding source ports in firewalls is called bad configuration and it can help attackers to easily evade firewall by putting almost negligible efforts. Many Firewall administrators configure firewalls with rules allowing incoming traffic from outside world that originate from specific ports like 80(http) ,443(https) ,53(DNS) ,25(telnet) etc.
We can easily configure custom ports in NMAP and push traffic from a specific source port (using option –source-port <n>) to evade or bypass this type of configuration. You can do by running below command in Kali Linux terminal :
nmap 192.168.56.102 -p 80 –source-port 53

Above command is forcing NMAP to originate traffic from source port 53 and send it to port 80.
Evading Firewalls by sending Custom size Packets :
Most firewall administrators are aware about NMAP and other Port Scanners. NMAP and other port scanners sends packets of specific size by default. So most firewall admins have configured firewall rules to filter out these packets. In order to evade or bypass this type of detection, we can easily configure NMAP to send custom packets using inbuilt parameter called –data-length in NMAP.
Below is sample command that can be issued in terminal to evade such restrictions :
nmap 192.168.56.102 -p 80 –data-length 40

Above command basically send 40 byte packets to target server instead on standard data packets.
Bypassing Firewall by spoofing MAC Address in NMAP :
This is another tricky way to evade firewalls which have rules configured in target server to allow only network packets from specific MAC addresses only. We can easily spoof MAC address using NMAP by using command –spoof-mac.
Below is sample to evade firewall by spoofing mac address :
nmap -sT –spoof-mac CISCO 192.168.56.102 -p 80

That’s it for today !!
Hope you all have enjoyed different ways to evade web application firewall and IPS using NMAP.